Email Delivery Issue: The account or domain may not exist, they may be blacklisted, or missing the proper DNS entries
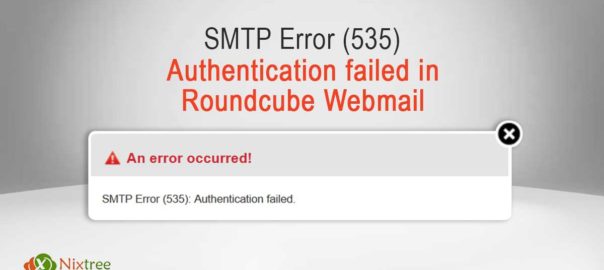
Nixtree Team comes across a wide range of issues to offer appropriate solutions to our clients. There was one interesting one. Our client faced the following error, while sending mail to another domain. This message wasRead More…