SSL/TLS Protocols and Ciphers
SSL/TLS Protocols
SSL (Secure Socket Layer) and TLS (Transport Layer Security) are most popular cryptographic protocols that are used to secure web communications with integrity, security, and flexible against unauthorized tampering. Encryption is necessary in order to communicate securely over the internet, SSL/TLS protocol used to establish secure connections between clients and servers over the internet, ensuring that the information relayed is encrypted and unable to be read by an external third party. SSL was the predecessor of TLS. SSL 2.0 was first released in February 1995 (SSL 1.0 was never publicly released because of security flaws). Although SSL 2.0 was publicly released, it also contained security flaws and was quickly replaced by SSL 3.0 in 1996. Then, in 1999, the first version of TLS (1.0) was released as an upgrade to SSL 3.0. Since then, there have been three more TLS releases, with the most recent release being TLS 1.3 in August 2018. The web connections are completely possible without TLS to secure them. However, without a security protocol in place, the communication would be revealed completely open to external access. If a browser connected to the website of an online store, and a user need to login with his credentials, those credentials could easily be lifted by an observing party. TLS, at its core, serves to provide end-to-end encryption for all data transmitted from one point to another, and uses cryptography to ensure that only the two transacting servers are capable of reading this information. Every service in the world now mandates that connections are secure by TLS – leading browsers do not allow users to access websites without a valid TLS connection.
SSL/TLS Ciphers
Cipher suites are sets of instructions which defines how to secure a network through SSL/TLS. They provide essential information on how to communicate secure data when using HTTPS, FTPS, SMTP and other network protocols. This information takes the form of algorithms and protocols that help determine how a web server secures a client’s web traffic. Cipher suites dictate which of these algorithms the server should use to make a secure and reliable connection.
Let’s see different Algorithms that Cipher uses:
Key Exchange Algorithm
For the insurance of data confidentiality during the transmission of data via different secure file transfer protocols like SFTP & HTTPS, the data has to be encrypted. This process requires that the two communicating parties have a shared key to both encrypt as well as decrypt the data. This type of encryption scheme is known as symmetric encryption.
Symmetric encryption does have its weaknesses, however. If attackers are able to get the shared key, then they can easily decrypt all the data. As a result, the industry developed key exchange protocols for the secure exchange of symmetric keys over insecure networks. These protocols are known as key exchange algorithms and include RSA, DH, ECDH and ECDHE.
Authentication Algorithm
To ensure the correct and secure transfer of data, a web server needs to verify the identity of the user who is receiving the data. Usually, this process involves the user inputting a set of credentials including a username and password. To facilitate this authentication process, cipher suites employ an authentication algorithm such as RSA, DSA and ECDSA.
Bulk Data Encryption
To ensure the secure transfer of data, cipher suites come with a bulk data encryption algorithm. AES, 3DES and CAMELLA are some of the most common algorithms in this category. As noted by Microsoft, a bulk encryption key is generated by hashing one of the MAC keys using CryptHashSessionKey together with the message contents and other data.
Message Authentication Code (MAC) Algorithm
Message Authentication Code (MAC) algorithm is a piece of information that is sent along with the message content for the purpose of authenticating the message. The sender and the receiver share a common key for the MAC algorithm to work. But this method comes with a disadvantage: it can’t protect against the intentional change of authentication codes. In certain cases, an intruder could change the message, then calculate a new checksum and eventually replace the original checksum with a new value. An ordinary cyclic redundancy check (CRC) algorithm can help, but it’s useful for detecting only randomly damaged parts of messages and not intentional changes made by the attacker. Some of the most common examples of this algorithm are SHA and MD5.
Cipher suite is a combination of Algorithm names which defines the rules of encryptions. Which looks like For eg: DHE_RSA_AES256_SHA256. This particular cipher suite uses DHE for its key exchange algorithm, RSA as its authentication algorithm, AES256 for its bulk data encryption algorithm, and SHA256 for its Message Authentication Code (MAC) algorithm.
How does SSL/TLS Encryption works?
TLS Handshake
When two systems attempt to connect via TLS, each system will verify that the other supports TLS. This process is called the TLS handshake, and it is here that both servers upon the TLS version, encryption algorithm, cipher suite etc. that will be used in the procedure. Once a TLS handshake has been successfully executed, both systems start exchanging data on a secure line. Every TLS handshake follows the same basic steps. For example, let’s assume a browser (a client) is attempting to connect to a server, which hosts a website: The client requests the server to open a secure line, and the server responds by displaying a list of TLS versions and cipher suites it is compatible with. Once they agree upon common ones to use in the transaction, they begin the handshake. The server sends a copy of its public key, attached to its digital certificate, to the client. The client checks the certificate to verify that the server is legitimate, and if it is, proceeds with the transaction. The client uses the server’s public key and its private key to encrypt a ‘session key’ which is a key that will be used by both parties to encrypt and decrypt information in this particular session. The session key becomes invalid as soon as the connection is terminated. Both parties test the connection by sending each other encrypted messages. If the other can decrypt them using the session key, the connection has been successfully secured.
Asymmetric vs. Symmetric Encryption
Asymmetric encryption was used to create the session key. But from that point onwards, the session key was used to bilaterally encrypt and decrypt the entire information flow between both parties. Here’s why: Asymmetric encryption is mathematically resource-intensive. The encryption-decryption operations involving two keys from both parties takes a heavy toll on the processing unit powering this process. If a system were configured to handle an entire connection this way – by using a public key to encrypt and a private key to decrypt it – it would probably give out within the first few minutes. It’s much more secure than its symmetric counterpart, but cannot be facilitated in an efficient manner. However, symmetric encryption, which makes use of a single, shared key to encrypt and decrypt, is not that resource-intensive. This is precisely why asymmetric encryption is used to establish a secure link between client and server, and used to generate the session key which, in theory, only those two parties can possibly know about. Now, symmetric encryption can be used to secure the connection, given the additional layer of security added to it by the first step.
How they important today?
Most important aspects of having an SSL Certificate is the protection of your valuable data. When you install an SSL Certificate, it protects your server-client interactions and encrypts every bit of your information HTTPS-secured websites are one of the topmost ranking factors for Google. SEO experts have demonstrated this in their findings. In 2018, Google announced its decision to flag any site without an SSL/TCI Certificate.
TLS has the following benefits:
-
The contents of the connection remain encrypted, private, and fully secure – and cannot be easily deciphered by malicious actors.
-
The connection is only made if it is reliable – this reliability check is a part of TLS communications, and is enforced by the exchange of a Message Authentication Code.
-
The use of PKI and TLS certificates ensures that the identities of both communicating parties are verified.
How to identify the Cipher used by an HTTPS Connection
Find the Cipher in Internet Explorer
- Launch Internet Explorer.
- Enter the URL you wish to check in the browser.
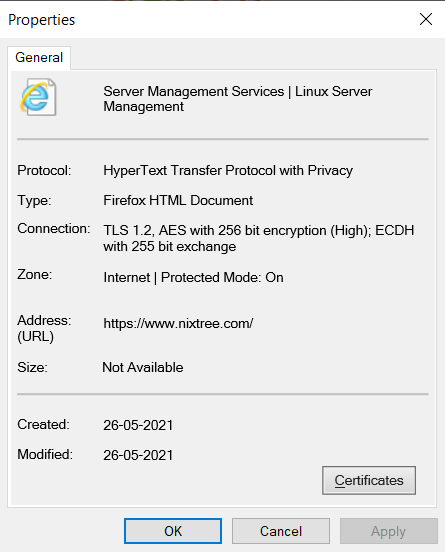
- Right-click the page or select the Page drop-down menu, and select Properties.
- In the new window, look for the Connection section. This will describe the version of TLS or SSL used.
Find the Cipher in Chrome
- Launch Chrome.
- Enter the URL you wish to check in the browser.
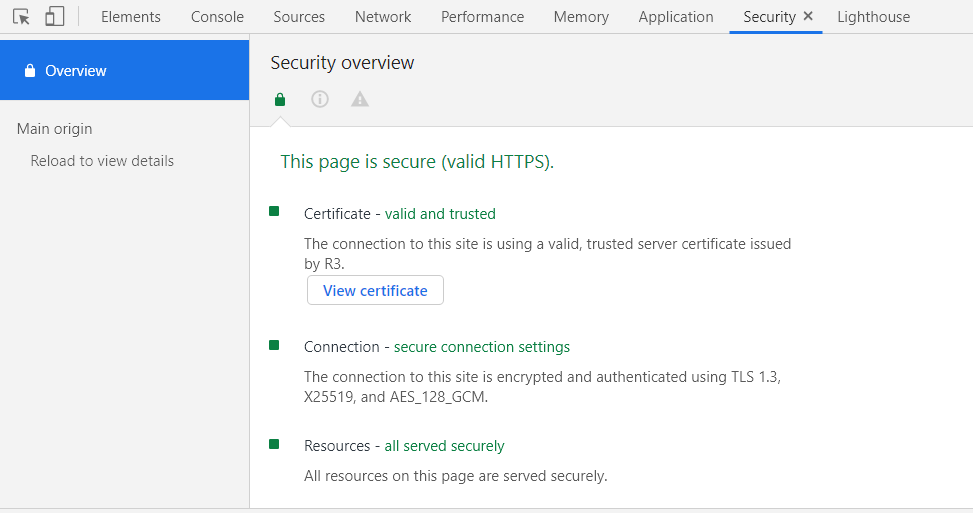
- Click on the ellipsis located on the top-right in the browser.
- Select More tools > Developer tools > Security
Find the Cipher in FireFox
- Launch FireFox.
- Enter the URL you wish to check in the browser.
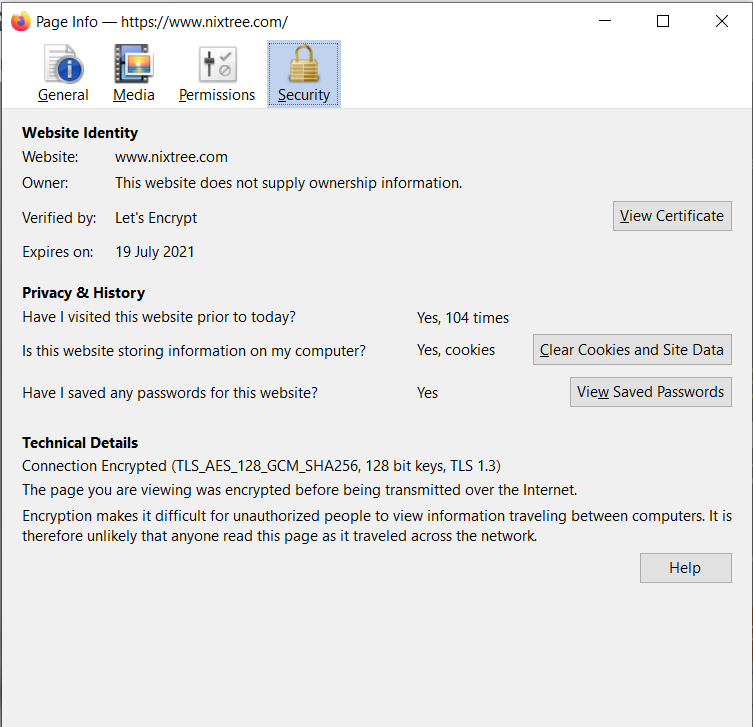
- In the address bar, click the icon to the left of the URL.
- Now click on More Information.
Conclusion
With the evolution of the internet, the solutions for better protection of websites increase. SSL/TLS are mainly for securing your data. It is unlikely that an SSL can be hacked, but it’s not impossible. The chances of an SSL hack are very slim. However, just because you’ve installed an SSL certificate doesn’t mean you are completely free from other software vulnerabilities.
Facebook Comments