Configure SSH Key based authentication from Linux and Windows system
Secure Shell (SSH)
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. When working with a Linux server, chances are, you will spend most of your time in a terminal session connected to your server through SSH. There are different ways to login into the server using ssh and here I am discussing about the ssh key based authentication.
SSH Key Based Authentication
Key-based authentication is the most secure mode of authentication.Instead of connecting through login/password to a remote host, SSH allows you to use key-based authentication.
Key-based authentication uses two keys, one “public” key that anyone is allowed to see, and another “private” key that only the owner is allowed to see. To communicate securely using key-based authentication, one needs to create a key pair, securely store the private key on the computer one wants to log in from, and store the public key on the computer one wants to log in to.
Key-based authentication has several advantages over password authentication.
How to setup key based login from Linux system
Generate Key Pair
You can generate key pair from linux system using the following command;
# ssh-keygen -t rsa
No need to provide passphrase, if you need additional security, you can give passphrase. Once you provided passphrase, you will ask for passphrase while logging into the remote server after the key’s are setup, otherwise you can login without any password or passphrase prompt.
By default following are the path for key pairs.
Private key : /home/nixtree/.ssh/id_rsa.
Public key : /home/nixtree/.ssh/id_rsa.pub.
Copy Public key to remote server
-
- Copy public key manually
Add public key to the following file as new line. ~/.ssh/authorized_keys
-
- Copy public key using ssh-copy-id command
ssh-copy-id user@server1.example.com
if you are using custom location for key pairs, you can use the switch “-i” to mention the key
ssh-copy-id -i /home/nixtree/.ssh/id_rsa.pub user@server1.example.com
Now try logging into the machine, with the following command and check the logins working or not.
ssh user@server1.example.com
if you are using custom location for key pairs, you can use the switch “-i” to mention the key
ssh -i /home/nixtree/.ssh/id_rsa user@server1.example.com
How to setup key based login from Windows system
For accessing a linux server from windows, we need to download putty. PuTTY is an SSH client that is available for Windows and Linux.
-
- Download additional software called PuTTYgen and PuTTY from
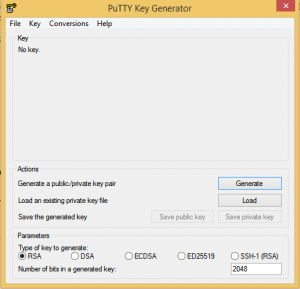
link here - Launch Puttygen tool and hit the Generate button
- Download additional software called PuTTYgen and PuTTY from
-
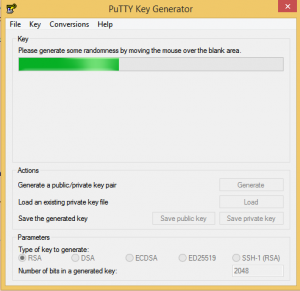
- When the phase is like the below image, make sure to move your mouse over and over to boost generator
-
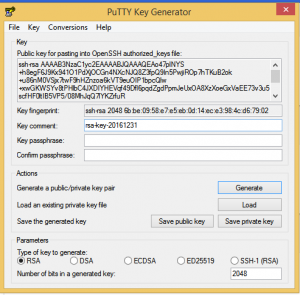
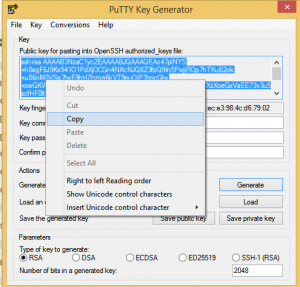
- Once it is done,it will look like below image
-
- Copy the generated key from puttygen to the file “~/.ssh/authorized_keys” in the remote linux server.
-
- Go back to Puttygen and save the private Key and public key.
Save public key as .txt and private key as .ppk
- Now, we need to configure putty.For that open putty Goto > SSH > Auth and Click the Browse button and locate the private key (.ppk) that you have saved private key and click open
- Now go back to main page on putty and type hostname and its corresponding SSH port number and Click Open.You will be logged into server without asking for password.
As an additional security you can do the following tweaks in the ssh configuration for additional security.
- Change ssh port to a custom port
- Disable root login and add an admin login and setup sudo access
- Disable password authentication and use only key based authentication
- Restrict ssh access from specific ip’s only.
If you are looking for securing the ssh or the entire server, you can contact our support for more details. Or you can select our Server management , so that we will do these hardening in the initial server setup.