How to find Spamming in cPanel
cPanel is a Linux based web hosting control panel that provides a graphical interface and automation tools designed to simplify the process of hosting a web site. cPanel is one of the commonly used web hosting control panel. cPanel will install all the necessary software, that are required for domain hosting. Spamming in cPanel is one of the common issues you might encounter. Spamming means flooding the Internet with many copies of the same message, in an attempt to force the message on people who would not otherwise choose to receive it. Most spam is commercial advertising, often for dubious products, get-rich-quick schemes, or quasi-legal services.
cPanel uses exim as the mail server, so I am referring to find the spamming in cPanel with exim as mail server.
Spamming in cPanel
Hackers will try to send spam emails through our mail server (exim ) without our knowledge. In most cases they will make this possible by using the vulnerabilities in websites codes which is used by us. Cms like wordpress, joomla and their themes, plugins will have their own vulnerabilities. The hackers will find the versions of the cms and plugins installed and they know the vulnerabilities related with the respective version. The developers will patch these products by releasing the latest updates. So first step to prevent spamming is update these cms and its components to the latest versions.
If we still suffering with spamming, we can follow basic steps below to find out the spam source. In most cases, it will be a php.
Analyze Spam headers
First we have to check the mail queue and find out how many mails are there stuck in the queue .Also we can find which account is sending spam mails and to which account .
$ exim -bpc # This command gives the count of mails in the queue. $ exim -bp # This command shows details of mails in the queue.
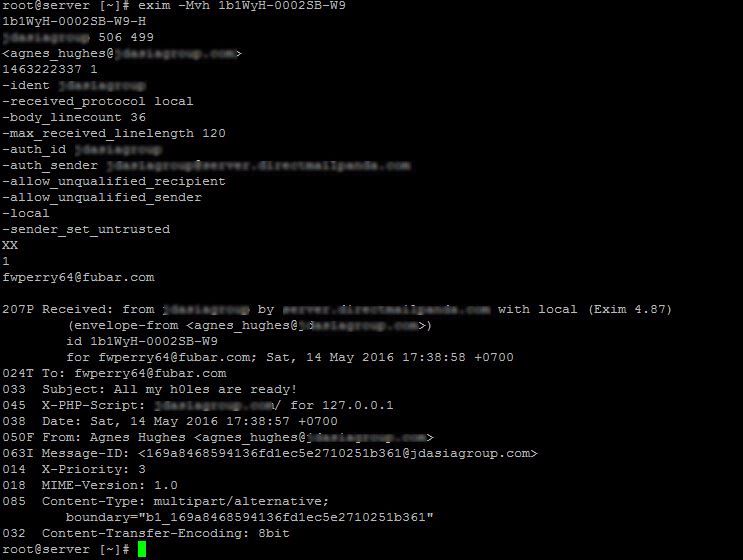
Check the below image, it is one mail entry from the “exim -bp” command. And following are the description of each field.
Image 1
Note: Due to security reasons some of the fields are erased.
47h ==> This denotes how much time the message has been stuck in the queue.
1.3K ==> This is the size of the message ,here it is 1.3 Kilobytes.
1b1WyH-0002SB-W9 ==> This is is the message ID.
This is something needed for debugging the spamming issue.
agnes_hughes@example.com ==> This is the account from which spam mail is sent.
(the blurred part after agnes_hughes)
techno ==> This is the account username which is being used for spamming.
(the blurred part in bracket)
fwperry64@fubarapi.com ==> This is the email account to which spam mails are sent.
Let’s see how we can get more details about the spamming by analyzing the header details of the mail. Headers contain tracking information for an individual email, detailing the path a message took as it crossed mail servers.
The “Image 1” as reference for commands.
$ exim -Mvh message_id # command to check the header details.
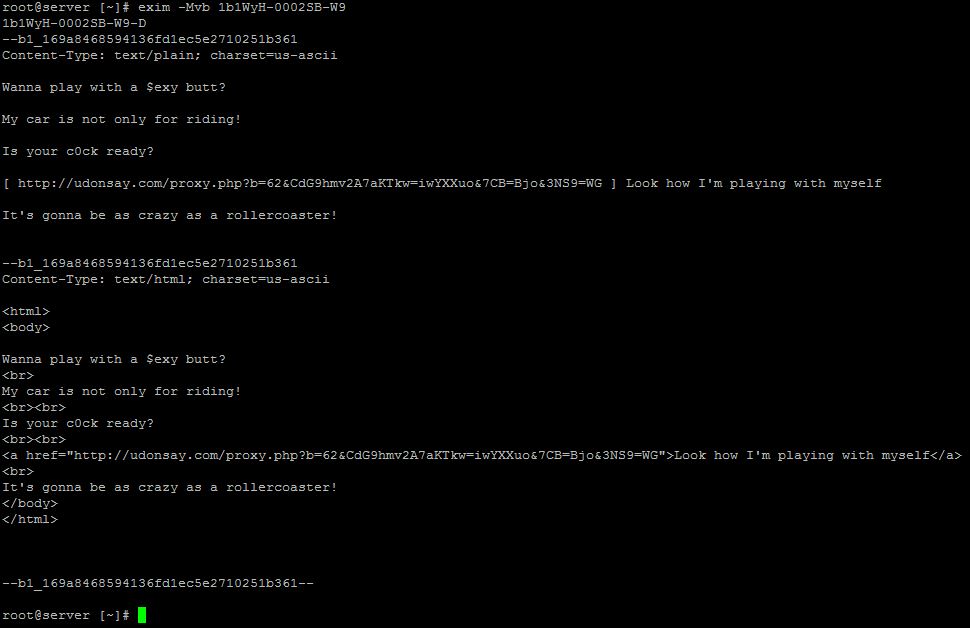
Check the below image with the command outout with the header details of one spam mail.
Image 2
You can analyze the above header and identify the message is a spam or not. From the above header, we can claim it is a spam by checking the subject itself. The entry “X-PHP-Script” will give the path of the from which the script is sending the mail. This will be shown in header only if we have mailheader php module is enabled using easyapche script. Not always X-PHP Script shown will be on spam mails, there may be instance that newsletters are sent using script. You may need to manualy check it and verify the same.
If you still feel the subject of the mail is genuine and X-PHP Script is not shown, then the next step is to check the body of the message .
$ exim -Mvb message_id # Command to check the body of the message .
Image 3
You can check the bosy of the message form the above image ( “Image 3” ). You can check the content of the mail to identify it is spam or not. Most of the spams are either adult related or asking credit card or bank details. If you still have doubt whether the message is spam or not check the body of the content and it is related to the site to verify it is spam or not. If still it is not verified, check with the site owner to verify it is genuine or not.
Now you get a basic idea about, how to find spamming from mail queue.
Different types of spamming
- Account compromised
- Spamming through scripts
Account compromised
This is a case in which someone has got access to your email account by knowing your password (by guessing your password or by some other way). Resetting the password with a strong password ( with alpha numeric characters ) and educate the customer to avoid using common passwords. Clear the mails from the queue after password is reset. Also restart exim to disconnect all the connected sections.
Spamming through scripts
This is something that usually happens when account is compromised. This happens mostly in accounts that use CMS(Content Management Systems) like wordpress, joomla etc.. In this spammer has compromised your account using the vulnerability in the application and upload a script for sending spam mails.
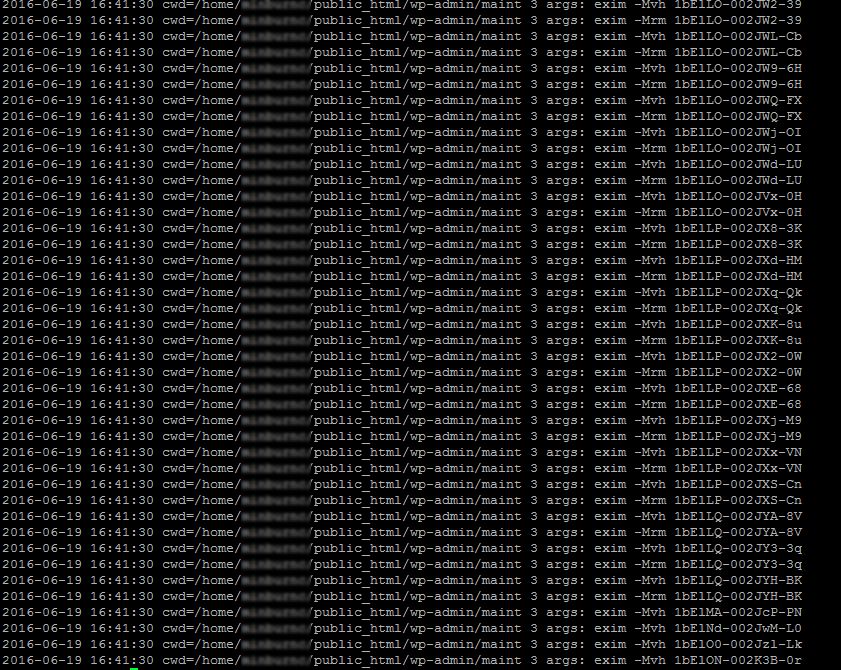
You can analyze the exim log to find the spammer. All the mails sending from the server are logged, so we can get the details of the spamming script. In exim there is a line containing the word “cwd”, means current working directory. So this show the path from where the mails sending script resides. To find the location of the script use the following command :
#tail -3000 /var/log/exim_mainlog | grep "cwd=/home/"
Used “cwd=/home/” to avoid getting the other log entries which are genuine mails. Check the mail logs for more details.
The above command will give you the location of the script that is seding mails from the server. The location will contain a mailer script, which is sending mails. Find the mailer script and remove if it is suspicious. Not all the php mailer script are suspicious, some of the forums are sending mails using php scripts, so just confirm before removing the script. You will get a result similar to the following;
Image 4
Once the location of the spamming script is located, then you can check the access_log for the respective domain for “POST” requests. The php scripts are sending mails with the “POST” request. By checking the post request, you can confirm the file from which the mails are sending. Once deleted/null rooted the vulnerable file.
Null root the spam script so that it won’t send spam mails again. To null root the file use the following two commands :
chmod 000 filename.php chown root:root filename.php
Once the suspected files are null rooted/ deleted. Next step is to find the way the suspected files are uploaded. If it is due to any vulnerability, fix that vulnerabilities to avoid uploading the spamming script again and sending spam mails again.
Spam Investigation
Just deleting the spam script will not fix the issues, it is just the first step. Finding the root cause of the issue and find a resolution. And take preventive actions to avoid this in future. If you are looking for any Spam investigation Service, you can contact “Nixtree Support” for more details.
We are one of the experts in cPanel Server Management, and we understand how to handle cPanel server in its best capacity possible, utilizing all cPanel server options. We offer a wide range of server administration works related to cPanel Server Management.